

Encryption software is the only line of defense protecting sensitive data from hackers in the event of a data breach. It serves as the final line of defense preventing cybercriminals from utilizing potentially business-crushing and life-ruining information.
The following comes from an in-depth analysis of the best free encryption software options to protect online users in 2019:
On its most basic level, encryption serves as a process of transforming information into code that can only be deciphered by authorized parties. It helps users remain confident their information is safe no matter where it’s stored.
Encryption can be used to disguise data both at rest and in transit. Encrypted data at rest is usually stored on a hard drive or USB device. Data in transit refers to information being transferred across internet, telephone or intercom networks.
Users can review specific features for each encryption product. These ratings are scored 0 to 100 and require 5 responses to receive a rating.
|
FileVault |
Letsencrypt |
BitLocker |
Tor |
OpenSSL |
DiskCryptor |
|
|
Email Encryption |
n/a |
100 |
70 |
96 |
n/a |
|
|
Messaging Encryption |
96 |
67 |
96 |
n/a |
||
|
File Transfer Encryption |
n/a |
98 |
77 |
96 |
73 |
|
|
Data Encryption |
n/a |
99 |
76 |
93 |
96 |
|
|
Document Encryption |
97 |
98 |
63 |
94 |
n/a |
|
|
Full-Disk Encryption |
97 |
94 |
53 |
94 |
100 |
|
|
Authentication |
92 |
97 |
76 |
93 |
93 |
|
|
Policy Enforcement |
n/a |
74 |
85 |
n/a |
||
|
Access Management |
86 |
97 |
90 |
84 |
88 |
|
|
Backup |
84 |
61 |
90 |
66 |
||
|
Recovery |
82 |
53 |
93 |
77 |
||
|
File Management |
n/a |
61 |
88 |
n/a |
||
|
Anomaly Detection |
88 |
65 |
91 |
60 |
*Blanks represent product features with “Not enough data available.”
**n/a represents a feature the product does not offer.
The list we’ve outlined here includes any encryption software product with an available free offering. It should be noted that this does not include products that are only free on a temporary basis, such as limited trial versions for new users.
These products alone have well over 100 validated user reviews on G2 Crowd as of Dec. 18, 2018, and only represent a portion of the 100-plus server virtualization offerings listed on our platform.

Vendor: Apple
User Reviews: 29
Star Rating: 4.2 out of 5.0 stars
FileVault is the MacOS native disk encryption tool provided by Apple on its laptop and desktop devices. The tool has been included as a free application automatically installed on new Apple devices.
The product allows users to perform ad hoc full disk encryption at the user’s request. The product uses the Advanced Encryption Standard (AES), the highest-recommended encryption standard determined by the National Institute of Standards and Technology (NIST).
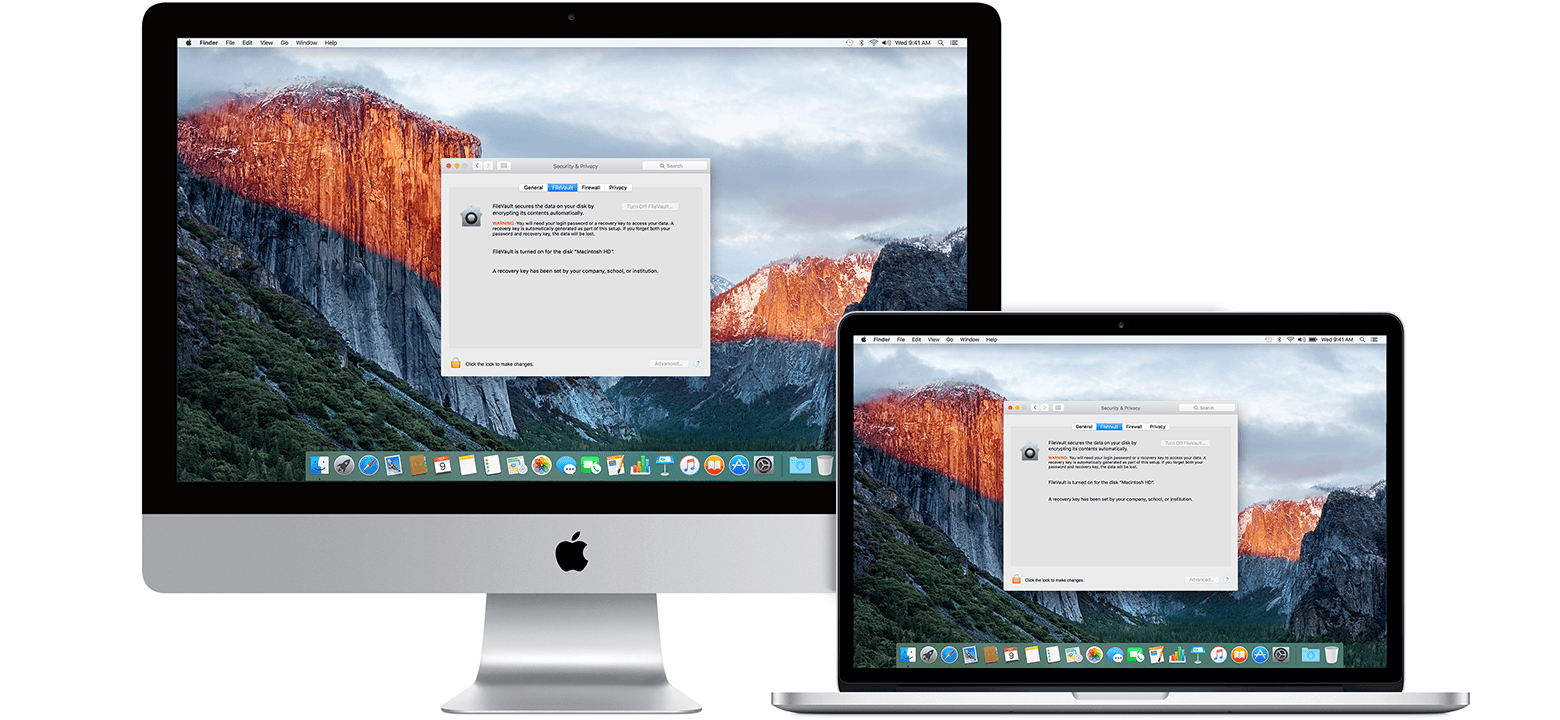
Image courtesy of Apple
What users say:
“The entire contents of the startup drive are encrypted. When your computer is powered off, the drive’s data is fully unrecoverable without a password. It also lets you use Find My Mac to wipe your drive in a matter of seconds remotely. If you are looking for a free and excellent solution for encrypting your end users’ data at rest, FileVault should be considered the industry standard for Mac users.”
— FileVault review

Vendor: Let’sEncrypt
User Reviews: 15
Star Rating: 4.8 out of 5.0 stars
Let'sEncrypt is a free and open-source tool used to generate and automate SSL/TLS certificates for websites. SSL/TLS certificates enable HTTPS, an encryption standard for secure networking.
This encryption technology is used to prevent eavesdropping on users and allows them to browse the web both securely and anonymously. Let’s Encrypt also provides domain validation to identify server administrator keys and ensure websites are validated upon its use.
What users say:
“It’s all free, very easy to install and set up. Instant verification and compatibility with all web hosting panels and web servers. It comes with a handy API to make certificates via plugins and its very efficient."
— Let’s Encrypt review
| Related: Learn more about SSL certificates and why your website needs one! |

Vendor: Microsoft
User Reviews: 48
Star Rating: 3.8 out of 5.0 stars
BitLocker can be best understood as the Windows version of FileVault. It also uses the AES encryption algorithm. It can utilize the same kind of 128- or 256-bit key. BitLocker is also included with every Microsoft Windows version since Windows Vista.
In addition to general disk encryption, BitLocker can be be used for device recovery through linked Active Directory accounts. Users can also enforce device management and administration standards through DMA port protection.
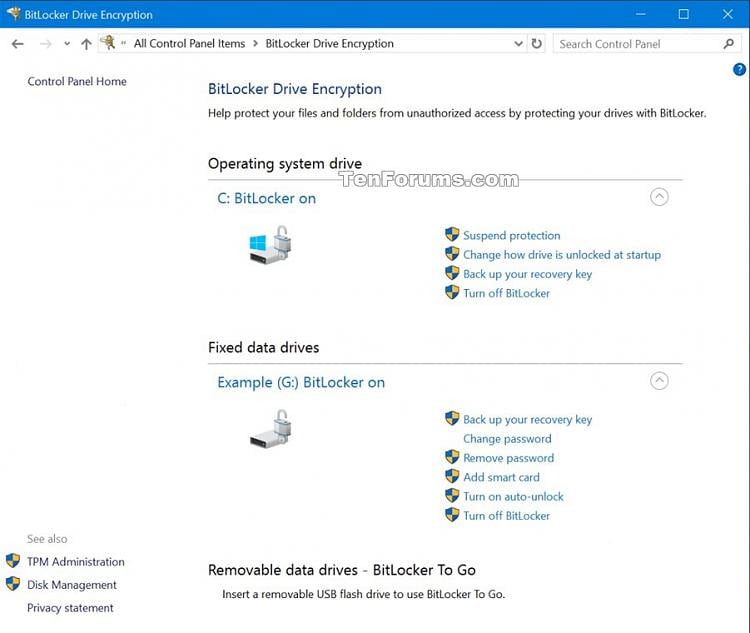
Image courtesy of Microsoft
What users say:
“The free version does the job well and requires no installation. I also like the ability for home users to unlock drives. It's a very simple encryption solution with an easy-to-use interface. I haven't needed any other encryption software to protect patient information. I can be confident that I'm using my home computer ethically without compromising patient safety and security.”
— BitLocker review
 Vendor: Tor
Vendor: Tor
User Reviews: 19
Star Rating: 4.0 out of 5.0 stars
Tor is a free anonymous web browsing tool that functions through a worldwide network of network overlay volunteers. It functions through the practice of “onion routing,” which adds multiple layers of encryption that are peeled away as communications approach their destination.
Tor has been a source of some controversy in the past since it was instrumental in the development of the darknet. Still, the encryption capabilities provided by Tor have numerous benefits to law abiding citizens, most importantly anonymity.

Image courtesy of Tor
What users say:
“Tor offers a completely secure and private browsing experience that allows you to be completely anonymous to all sites you visit. If you love being anonymous and hate targeted ads based on your location on websites, Tor is a great browser. It is free, so check it out!”
— Tor review

Vendor: OpenSSL
User Reviews: 13
Star Rating: 4.5 out of 5.0 star
OpenSSL is a library of encryption tools used for TLS and SSL protocol enforcement. OpenSSL was first released in 1998, and remains free and open source to this day.
OpenSSL is used to generate the certificates offered by vendors like Let’s Encrypt. The library supports a number of widely used cryptographic algorithms including AES, Blowfish, 3DES and many others.

Image courtesy of OpenSSL
What users say:
“What I like most about this tool is that it is free to use. We can help with the documentation to get started and start working. It is a bit complex at the beginning, we must take some time to study the documentation to be able to integrate it in a certain way, besides the updates of the versions can cause certain errors.”
— OpenSSL review
Vendor: Tor
User Reviews: 12
Star Rating: 4.4 out of 5.0 stars
DiskCryptor is a full-disk encryption tool for Windows operating systems. While the functionality is similar to that of BitLocker, DiskCryptor is free and open source.
DiskCryptor supports AES, Twofish and Serpent algorithms and supports external storage devices to encrypt CDs, DVDs, USB drives and external hard drives. Features of DiskCryptor include pre-boot authentication, hardware acceleration, file encryption and two-factor authentication.

Image courtesy of DiskCryptor
What users say:
“I recommend the program since the effectiveness of it is verifiable, in addition to offering an encryption procedure very easy for anyone with little knowledge in this activity, it is important to note that the best thing is that we are talking about a very complete program from the point of view of its functions, and that is also completely free, which offers an attractive alternative for any potential user who wants to use data encryption.”
— DiskCryptor review
Those researching free encryption products online can sift through hundreds of verified user reviews on G2 Crowd to find the best option. Check out the encryption software category where you can compare products, discover available features and read user reviews.
* Please note: Reviews may have been edited for spelling and grammar
Aaron has been researching security, cloud, and emerging technologies with G2 for more than half a decade. Over that time he's outlined, defined, and maintained a large portion of G2's taxonomy related to cybersecurity, infrastructure, development, and IT management markets. Aaron utilizes his relationships with vendors, subject-matter expertise, and familiarity with G2 data to help buyers and businesses better understand emerging challenges, solutions, and technologies. In his free time, Aaron enjoys photography, design, Chicago sports and lizards.
In today’s vast digitally-connected world, it can be difficult to maintain some privacy.
 by Devin Pickell
by Devin Pickell
Data security and protection are the secrets to success for many businesses, and cloud data...
 by Samudyata Bhat
by Samudyata Bhat
Data needs security, and security needs encryption.
 by Sagar Joshi
by Sagar Joshi
In today’s vast digitally-connected world, it can be difficult to maintain some privacy.
 by Devin Pickell
by Devin Pickell
Data security and protection are the secrets to success for many businesses, and cloud data...
 by Samudyata Bhat
by Samudyata Bhat
Never miss a post.
Subscribe to keep your fingers on the tech pulse.



